Read the intro for the Common Attacks room and continued to the next task.
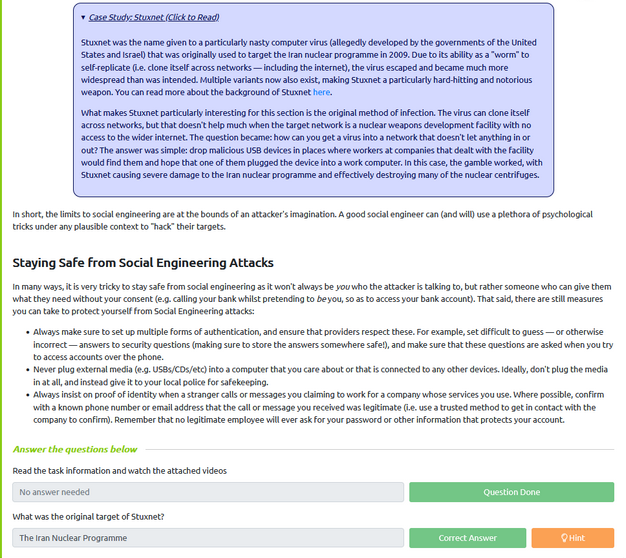
Read about what social engineering is, the forms and staying protected from it. Watched the videos demonstrating social engineering and the severity of what information can be obtained. Reading the Stuxnet Case Study provided the answer for the question: What was the original target of Stuxnet?
The answer is “The Iran Nuclear Programme.”
Read the information about phishing and the different types/subcategories. I clicked on the “Visit Site” button at the top of Task 3.
Determine if the email is safe or not:
Email 1
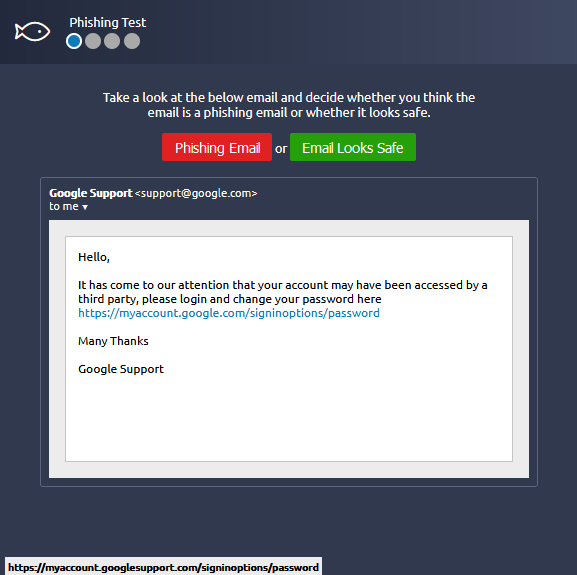
When hovering the pointer over the link the URL doesn’t match and should be approached with caution as a potential phishing email.
Email 2
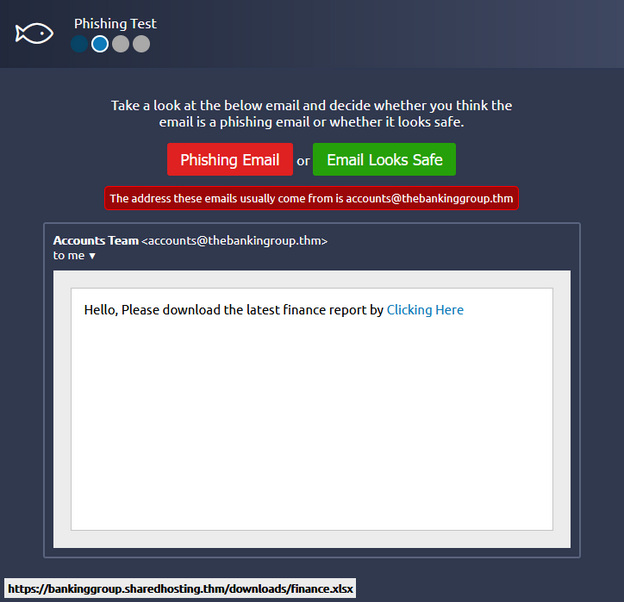
The sender’s email doesn’t match the official sender email. There should be two g’s. Also, the link doesn’t look safe. This proves the email to be a phishing email.
Email 3
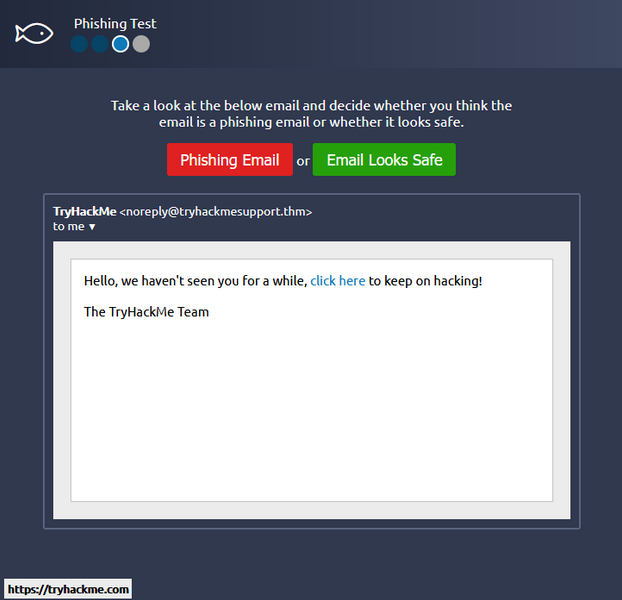
The sender looks official with no typos or unfamiliar words and the link is correct for the THM website confirming the email is safe.
Email 4
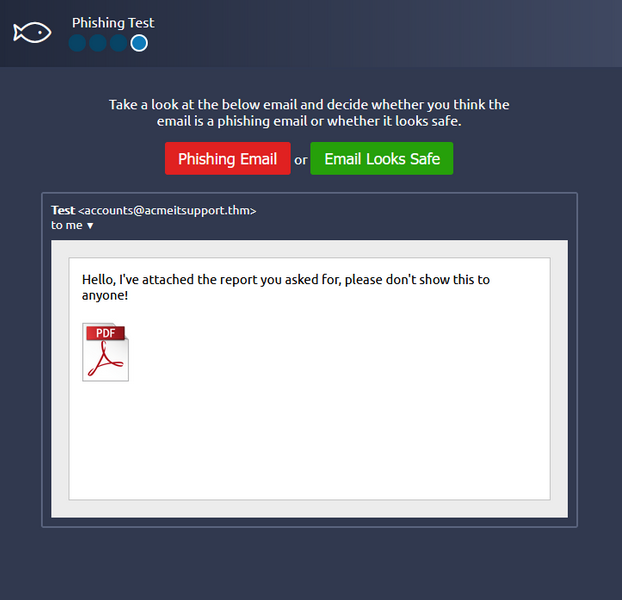
The sender is unfamiliar and so the PDF should be viewed as suspicious. This email is most likely a phishing email.
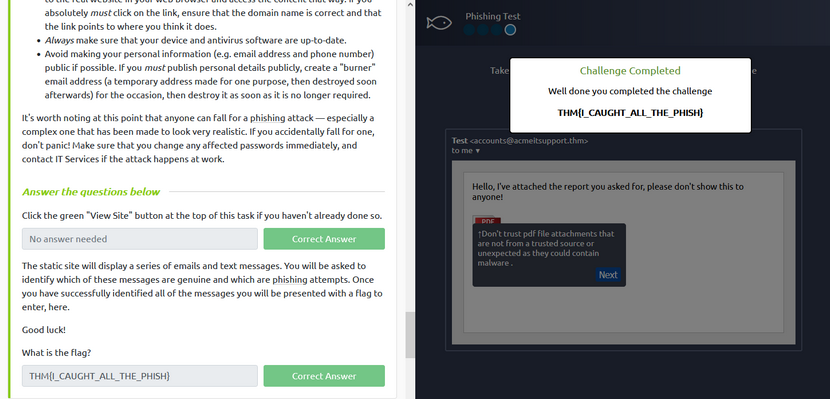
Finding the Flag:
After completing the Phishing Test, a flag is displayed to submit for the last question.
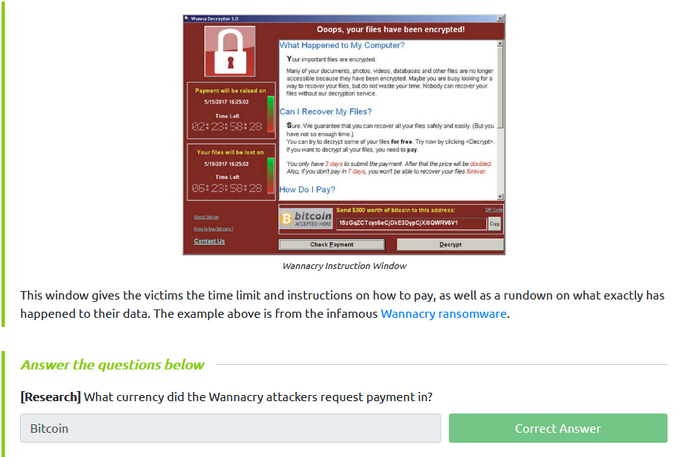
Read the information provided about malware and ransomware. By noticing the material states the example for ransomware is from Wannacry, I could identify that they wanted to be paid in Bitcoin. This answers the question: What currency did the Wannacry attackers request payment in?
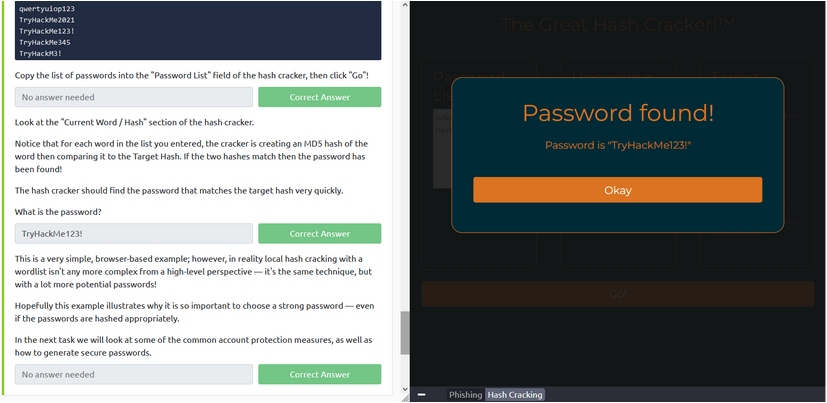
Read about password security, data breaches, and password attacks. After reading I clicked the “Visit Site” button.
Then I copied the password list onto the site and clicked “Go!” This generated the password which was “TryHackMe123!” I then continued to the next task.
Read about multi-factor and password managers and their importance. I then completed the question.
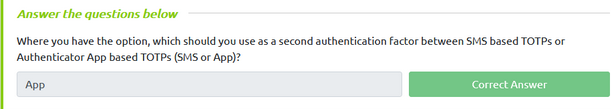
App was the answer because an App based TOTP is more secure as the code can’t be intercepted as with SMS based.
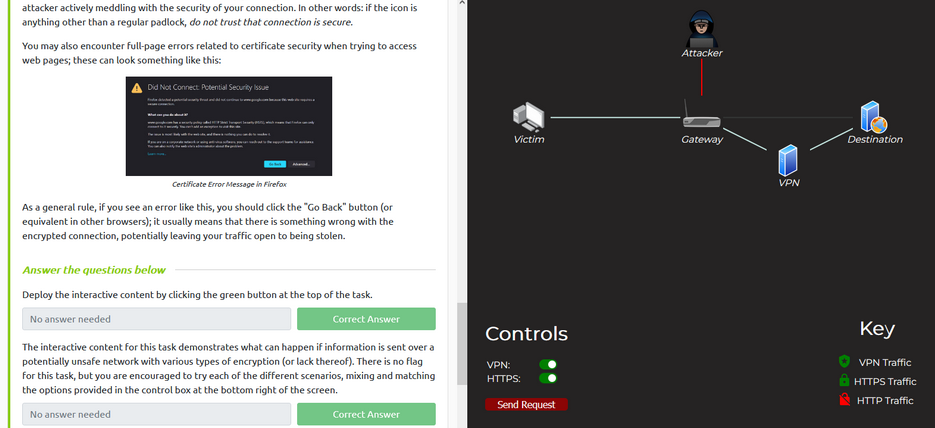
Read about the dangers of open/public networks and solutions (i.e. VPN). Read about HTTPS and what to be aware of. I clicked on the “Visit Site” button and viewed different scenarios of having a VPN and/or using a site with HTTPS.
Read about the rules for keeping backups of data.
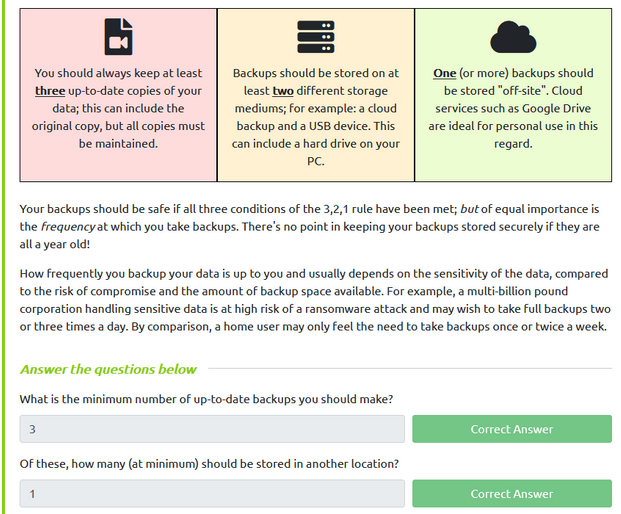
Answered the questions according to the 3,2,1 Rule.
Learned about patches and the importance of staying updated for systems and applications. Added myself to the “Blue” room on THM to complete at a later date.
Read the conclusion and completed the room.