Mobile devices are just as powerful as PCs and just as vulnerable too. We’re gonna learn about securing our mobile devices and how to analyze malware.
This task focuses on researching mobile malware. I used google to answer the questions.
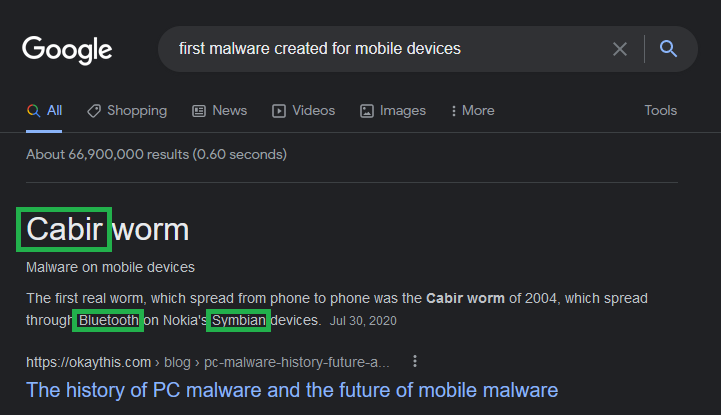
What is known as the first malware created to affect mobile devices? Cabir
What technology does this worm use to multiply? Bluetooth
What operating system did it infect? Symbian
I clicked the link to see if the message was discussed.
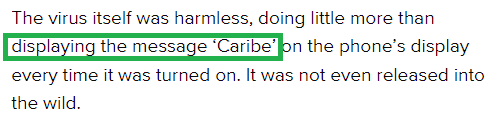
What message did it show on the screen of the infected mobile phone? Caribe
Task Completed!
I started the windows machine for this task in order to analyze a suspicious file. After a couple minutes the MobSF application launched and I dragged and dropped the suspicious file to be analyzed:
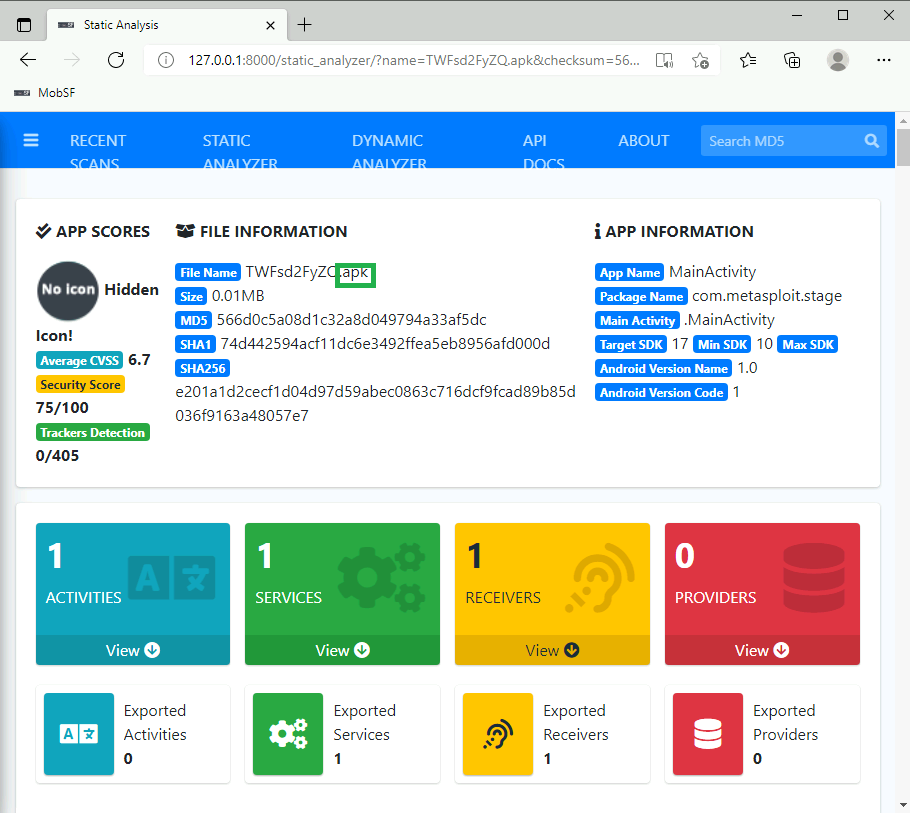
What is the format of the file? .apk
In order to decode the file name I searched “decode filename online” on Google and clicked the first link to see if it was helpful. After playing around with the tool option which is the decoding method, the Base64 Encoder/Decoder option provided this display:
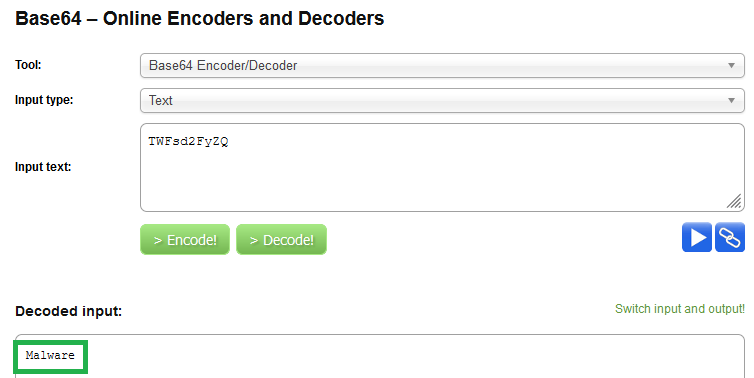
Decode the name of the sample. Malware
To answer the next question I knew that .apk files are for android devices.
Which is the target platform? Android
Task Completed!
To dig deeper into the analysis we have to make a file hash and input it into VirusTotal. I used the command ‘Get-FileHash [filename]’ and got the SHA256 hash for the file:
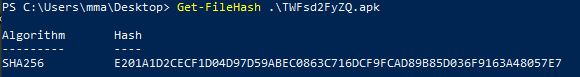
Here are the results in VirusTotal:
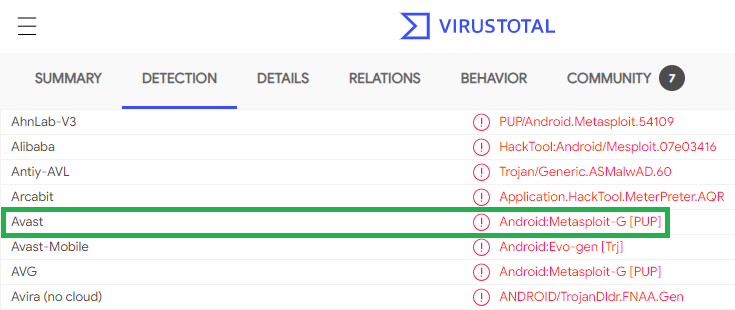
What does Avast-Mobile tell us about this software? Android:Metasploit-G [PUP]
Details/Android Info/Summary section:
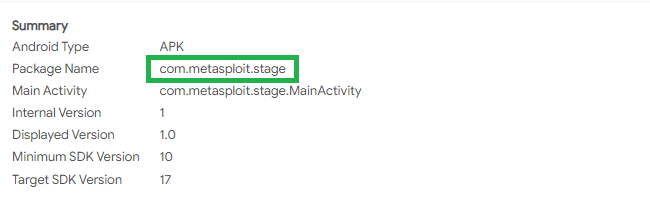
What program was used to create the malware? Metasploit
What is the package name? Com.metasploit.stage
Details/Basic Properties section:
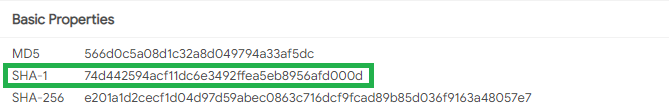
What is the SHA-1 signature? 74d442594acf11dc6e3492ffea5eb8956afd000d
Relations/Bundled Files:
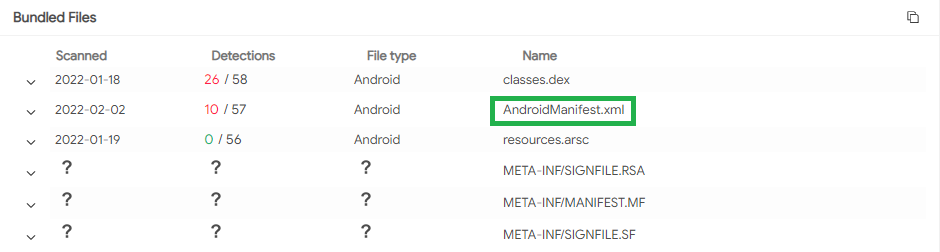
What is the unique XML file? Androidmanifest.xml
Details/Android Info/Permissions section:
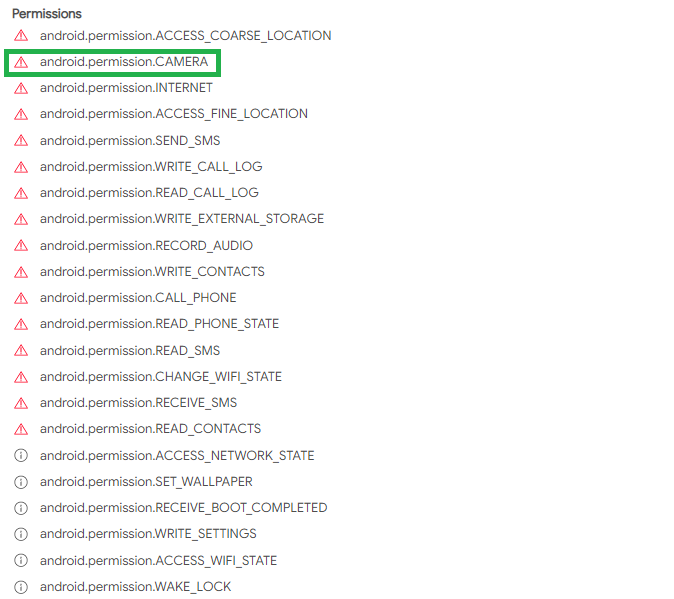
How many permissions are there inside? 22
Which permission allows the application to take pictures with the camera? android.permission.CAMERA
Community section:
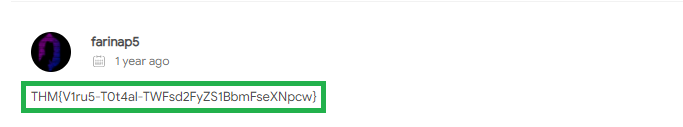
What is the message left by the community? THM{V1ru5-T0t4al-TWFsd2FyZS1BbmFseXNpcw}
Task Completed!
For this task we go back to MobSF to answer the provided questions.
In the Android API section:
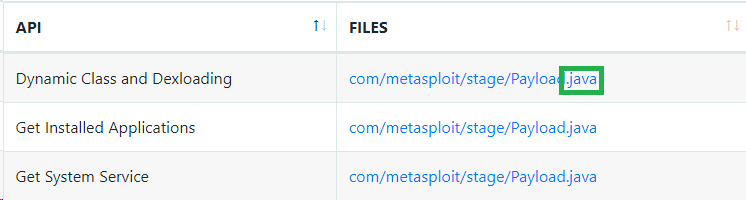
What is the programming language used to create the program? Java
Signer Certificate section:
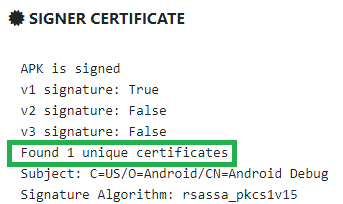
How many signatures does the package have? 1
In the section below the certificate is the answer to the next question:
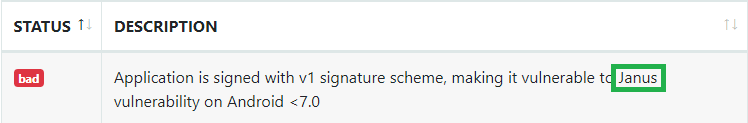
Application is signed with the v1 signature scheme, what is it vulnerable to on Android <7.0? Janus
Then I looked at the App Information at the top of the page:
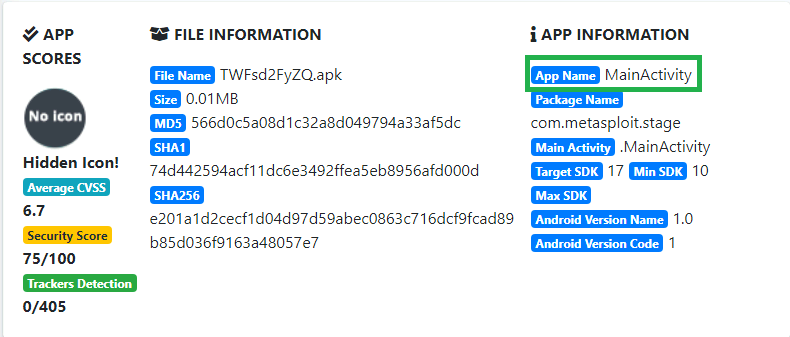
What is the App name? MainActivity
Then I looked at the Android API section again as it had a file used to ‘Get Installed Applications’. I clicked on the ‘Payload.java’ file to try and answer the next question:
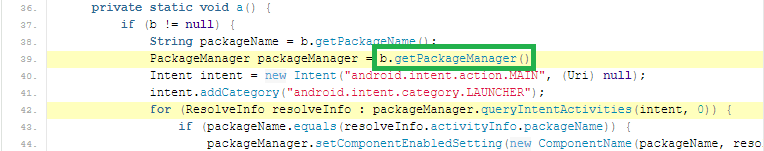
It looks like there is a function calling for the package manager, so it can see all the installed applications. What function is that? b.getPackageManager
Then we return to the Static Analysis and the Manifest Analysis section:
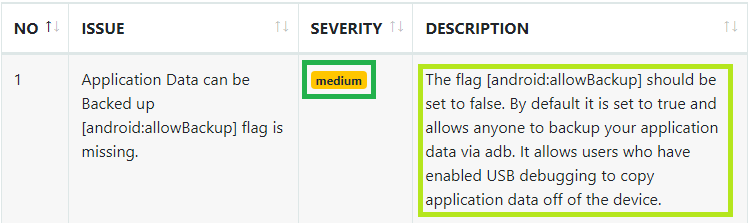
The flag "android:allowBackup" allows the user to backup application data via USB debugging. It is recommended that this be set as "False", even if by default it is "True".
What is the severity of this configuration? medium
Task Completed?
Now we’ll be analyzing the file ‘sample2.apk’. So I analyzed the file in MobSF to try and answer the questions and get a better look at the file’s intentions.
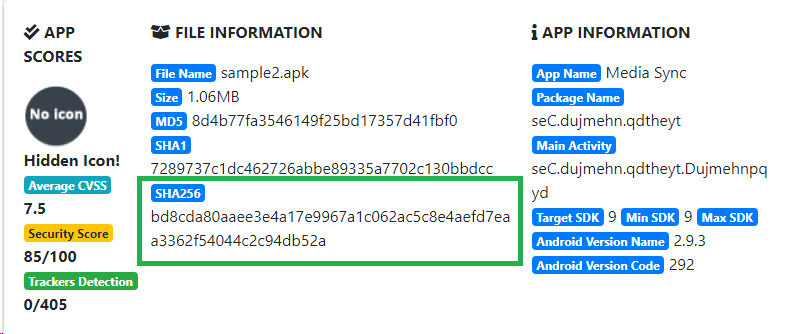
What is the SHA-256 hash of the file? Bd8cda80aaee3e4a17e9967a1c062ac5c8e4aefd7eaa3362f54044c2c94db52a
Then back to VirusTotal:
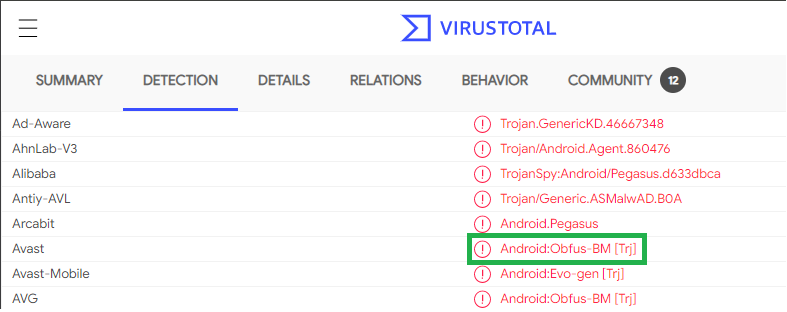
After finding the sample on VirusTotal, what does the “Avast” anti-virus engine recognize it as? Android:Obfus-BM [Trj]
Then I went to the Details tab to figure out the next question:
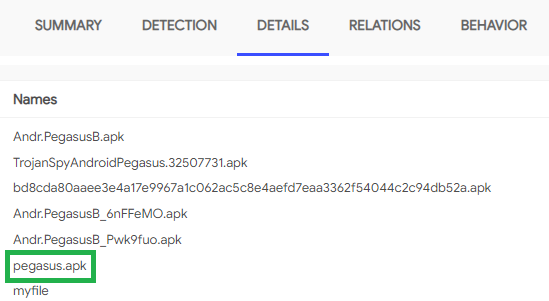
With what we have, try to find out the name of the sample. Pegasus
This is a pretty old malware that became news for spying journalists so to figure out what year this was I went to good ‘ol Google. I searched ‘Pegasus spyware history’ and skimmed the Wikipedia page. It was first developed in 2011 but wasn’t revealed until 2017 at the Security Analyst Summit after Google researchers discovered the android malware.
This became news for spying journalists, what year was that? 2017
Then I searched for ‘pegasus’ on MITRE ATT&CK to answer the next question.
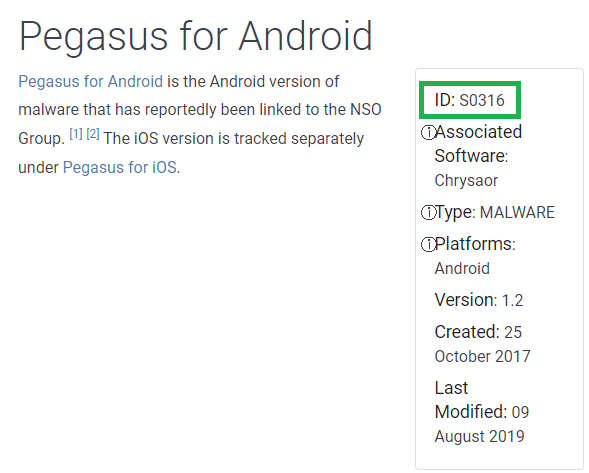
What is the ID of MITRE ATT&CK that is associated with our sample? S0316
Then I looked at the techniques the malware uses to escalate privileges:
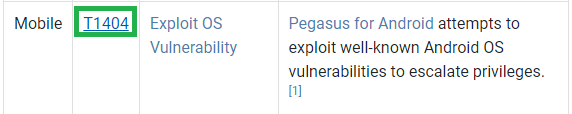
What technique has the ability to exploit OS vulnerabilities to escalate privileges? T1404
Now I headed back to MobSF to answer some more questions. First, I looked at the ‘Permissions’ section:
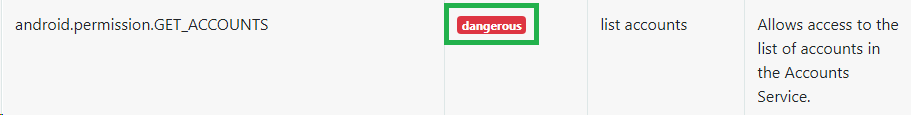
There is a permission that, when accepted, allows the application to access the list of accounts in the Accounts Service. What is the status shown by MobSF regarding this permission? (android.permission.GET.ACCOUNTS) dangerous
I then went to the ‘Files’ section:
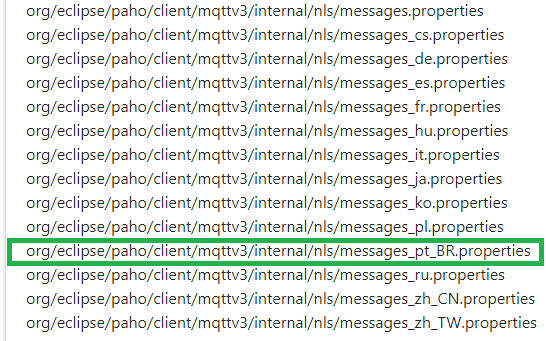
What org.eclipse.paho.client file refers to properties of Portuguese from Brazil (pt-br)? org/eclipse/paho/client/mqttv3/internal/nls/messages_pt_BR.properties
For the last question they ask for a way to identify a certain feature of pegasus.apk. I was able to find a feature relating to the question as well as an identifier in the ‘NIAP Analysis’ section:
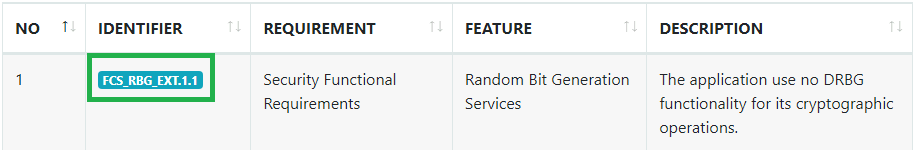
The malware has a special appeal for its safety and its internal components, reducing the risk of compromise. It has a functionality for its cryptographic operations with the feature of a random bit generation service. How can it be identified? FCS_RBG_EXT.1.1
Task Completed!
I now have a better understanding of what can be exploited on mobile devices with more sources to dig even deeper.
Room Completed!